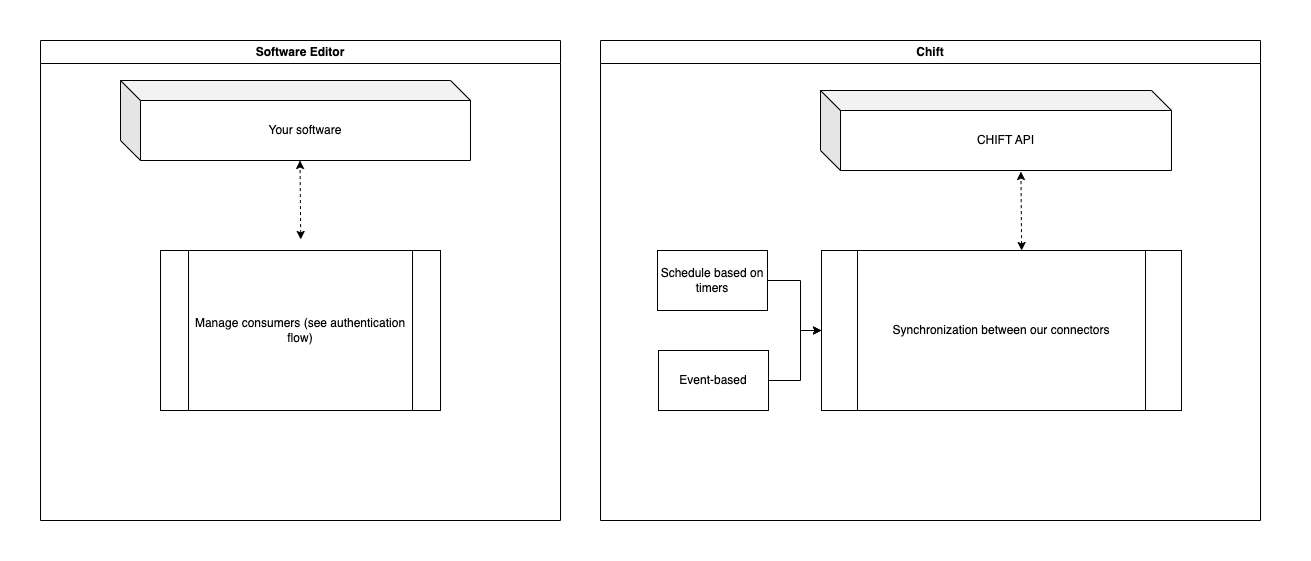
- Authentication workflow
- Easy way - you do the work
- Lazy way - we do it for you
Authentication workflow
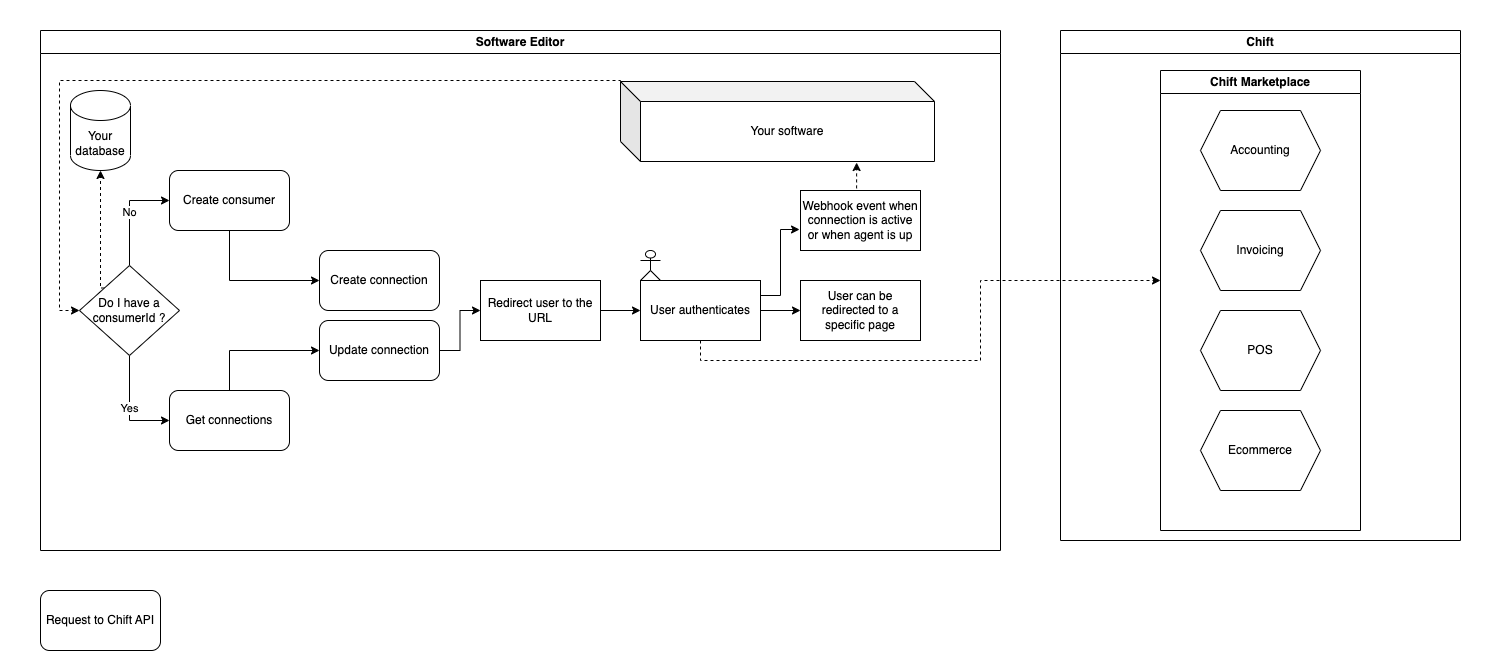
- From your software, you can initiate the integration for one of your customer.
- The consumerId is the link between your customer and Chift. You keep this in your database to be able to make requests to our API when required by your business case.
- Based on your consumerId, you receive a link that you can share with your customer to initiate a connection.
- Your users are redirected to Chift’s authentication page where they can connect to the softwares of your choice.
- Once the initial connection is setup, you can activate a webhook to receive asynchronously an event or your user can be redirected to the URL of your choice.
- Now you are ready to request our unified APIs.
Unifed API model
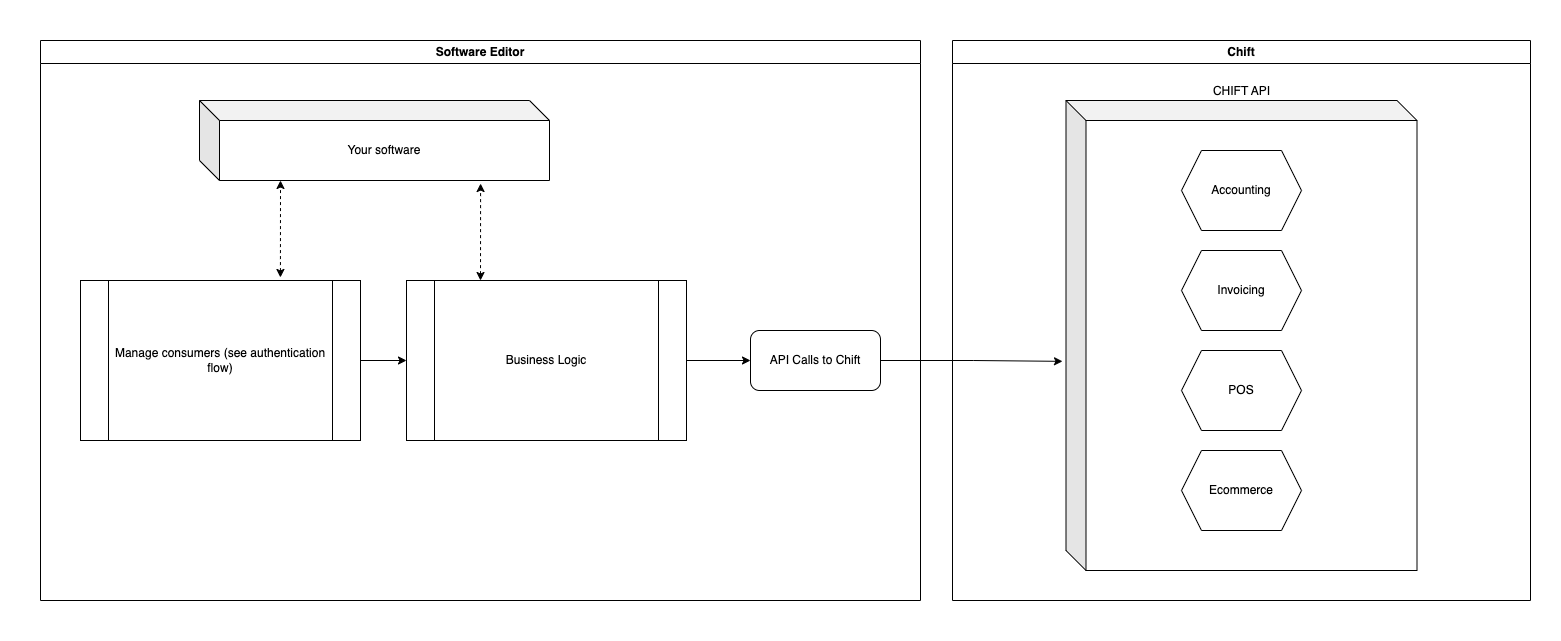
Sync model